Find and map your sensitive SAP data and benchmark your access risks
Understand, identify and map your Personally Identifiable Information (PII) with EPI-USE Labs’ SAP data privacy assessment service

Minimize risks of exposing sensitive data
Manage your data security effectively
Comply with global data privacy legislation
Data discovery, consulting & workshops
Data Privacy & Risk Assessment analysis
Why do you need to understand your sensitive SAP data?
Extensive sensitive data about your customers, vendors, and employees is held in your SAP system. When addressing your data privacy, taking the SAP data model into consideration is critical; if you update one field, it will populate the value in different places throughout your system. In our experience, one personally identifiable value can be replicated up to a 100 times throughout your system. With this depth of data, you need to change the values consistently throughout the system to comply with data privacy regulations. Also, many long-term SAP business users have developed customized functions, including custom tables storing data and facilitating processing, which expands the target for sensitive data.
Leveraging our decades of domain experience in the SAP data model, we can help you manage your sensitive data consistently between objects and systems.

PII data and global data privacy regulations
As well as the standard delivered data model which SAP provides, all clients customise their processes and data storage, replicating PII into custom tables, most without maintaining a PII data map. These tables have been built for efficiency, but new privacy laws present a challenge, as nobody knows all the places in which PII has been stored throughout SAP.
Global data privacy regulations include:
- GDPR (General Data Protection Regulation) in Europe
- CCPA (California), CPA (Colorado), CTDPA (Connecticut), CDPA (Indiana, Montana), ICDPA (Iowa), TIPA (Tennessee), TDPSA (Texas), UCPA (Utah), VCDPA (Virginia) in North America
- POPIA in South Africa
- PDPA in Thailand
- LGPD in Brazil
- PIPA in South Korea and Japan
- NZPA in New Zealand
- PIPEDA in Canada
Each of these regulations includes the 'right to access' and 'right to deletion / correction'. To comply, you need to understand and map the PII in your IT estate.
Comprehensive SAP data privacy assessment service
We can help you to understand and identify your Personally Identifiable Information (PII), and assess your access risks. Our comprehensive service covers:
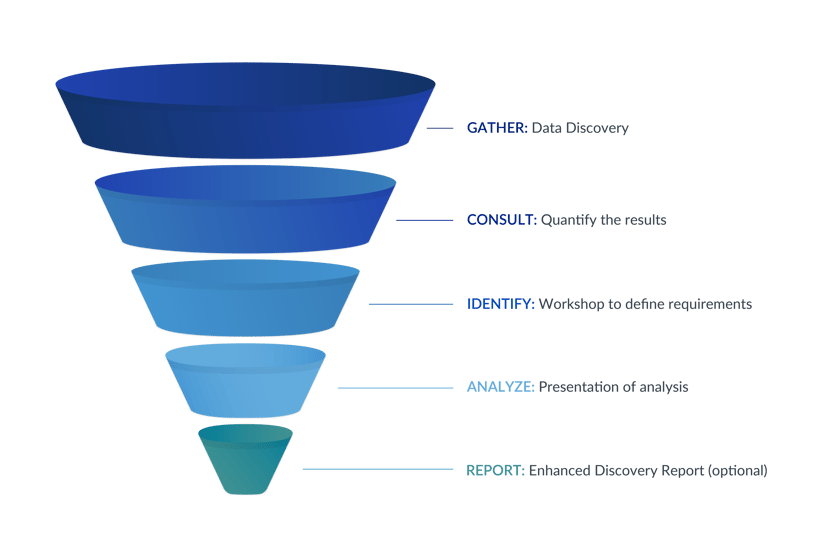
GATHER: Data Discovery
As an SAP development partner specializing in SAP data management, we have developed our own proprietary Business Object Definitions detailing the integration between objects and between systems. From this detailed table mapping, we have created a field-level integration map of all standard SAP PII fields.
Using this map, we have designed a Data Discovery program to analyze the Data Dictionary in your SAP system. It performs a wildcard search of sensitive data elements, and builds a list of tables and fields potentially containing PII. The tables are then validated to confirm they are populated.
Consult & Identify:
Consulting services and managed data privacy workshop
Our data privacy specialists will run a workshop with your functional team to define the requirements for all PII data types including:
Production data retention requirements, per data type
For instance, remove bank and family details immediately when an employee becomes inactive, contact details after five years and full redaction after 10 years
Landscape review and system data inheritance
Which systems will ingest the scrambled data and will scrambling impact this?
Non-production data scrambling
What actions should be taken per data type, and are there exceptions or conditions?
Redaction
What action should be taken in Production once a data subject becomes eligible for redaction?
Disclosure
Which data from SAP should be included in the Subject Access Request PDF?
Our trained consultants have experience in many industries globally. They understand the complexity of data privacy, and can share their extensive experience with you.
There is no license cost for this service, and we would expect a typical SAP ECC engagement to take five days, over a two-week period:
- Three days ‒ Data Discovery and technical system analysis
- One day ‒ Workshop with your business and compliance teams
- One day ‒ Documentation and presentation of results.
We recommend face-to-face workshops, but can work either remotely or on site.
Analyze:
SAP Data Privacy and Risk Assessment analysis
The output will be collated in our in-depth SAP Data Privacy and Risk Assessment analysis document, informing your business, compliance team, and data protection officers of the level of risk in your SAP environment.
This will be presented in a follow-up meeting with the project stakeholders, with an outline of costs for the delivery.
Report:
Enhanced Discovery Report (optional additional service)
With an additional two days’ input, we offer an Enhanced Discovery Report with our strategic partner Soterion, considering both your data privacy risk and access risk in the SAP system. Soterion focuses on building business-centric Governance, Risk and Compliance (GRC) solutions for SAP to enhance business accountability of risk.
A file export will be taken from your SAP instance and loaded to a temporary instance of Soterion, hosted in a local data center, to complete an analysis and present the results.
Soterion has a standard access risk rule-set. Whether you already run a GRC solution or not, these pre-built rules will measure your compliance status.
Highlights of the key insights provided as a part of this enhanced service:
Privacy data access risks
Most GRC solutions are focused on segregation of duties and fraud avoidance. Soterion performs these functions, and also has built a rule-set to analyze who has access to PII data.
Segregation of Duties (SoD)
Who has access to both submit and approve payments, for example? Soterion will identify all the users who hold conflicting access in the system.
Cross-legal jurisdiction data access
Can your users from the US access European employee and customer data, or vice versa? If yes, which users would be affected in creating a Data Shield?
Critical transaction risk
Who has direct access for table maintenance, or can run programs directly? Is Vendor and Customer maintenance restricted to the correct people?
With these reports and others, EPI-USE Labs and Soterion will provide you with a Benchmark Risk Assessment of both your data privacy and access risks, along with recommendations on how to address these risks.
How our clients succeed
JM's journey to a live, compliant GDPR solution
With the EPI-USE Labs’ approach, we can anonymise and redact sensitive data, meaning business transactions may stay in the system without being related to an identifiable individual. Now, when starting projects, we have frameworks for how to do information sensitivity and risk analyses, and from there come the requirements on the IT side, including the sensitivity of data – the complete information security perspective.
Richard Wenell, Head of IT department, JM
MAPA: Customized protection for sensitive SAP HCM data
.
Thanks to Data Secure, we can anonymize all sensitive SAP HCM data, such as employee-related data, in a very short time. The biggest advantage of Data Disclose is that data integrity is guaranteed; customers’ sensitive data is anonymized but all orders and items sold are still accessible. All test systems stay fully functional, and test orders are still editable.
Malte Podszus, Consultant FI/CO/HR, MAPA GmbH
How Endeavor improved their GRC compliance for SAP with Soterion
We have had very good results on our Access Review Management, which is now performed by our line managers with much less effort. With Soterion, we identified that many people had risk-bearing access that they no longer needed. Now, we have reduced our access risk footprint significantly. Our business users expressed their appreciation of having a tool that was much easier for them to work through, understand, and have visibility over the reviews.
Nick Achteberg, Senior Director Technical Services (SAP), Endeavor
Rabobank banks on EPI-USE Labs for data regulation compliance
Scrambling data was a time-consuming manual exercise which didn’t give us enough guarantees that sensitive data was securely scrambled. We wanted to be 100% confident that all sensitive data was masked. We needed a product that would remove the manual effort, allow us to schedule jobs and enable us to comply with regulations. That product proved to be Data Secure.
Jan Huizinga, Technical consultant, Rabobank
Want to know more?

Book your assessment
Minimize the risks of exposing your sensitive data, manage your data security and comply with global data privacy legislation with our SAP data privacy assessment service.

Explore our Data Privacy Suite
Our innovative data privacy and compliance solution helps companies with SAP® systems comply with legislation like
GDPR (the General Data Protection Regulation) and other data privacy legislation.
Get in touch
Find and map your sensitive SAP data and benchmark your access risks


