The majority of components making up a Governance, Risk and Compliance (GRC) solution are back-end type activities performed by GRC or SAP® security administrators. However, some GRC activities have a crucial touch point with business users of that functionality, namely:
-
SAP Access Risk Simulations (approval/rejection done by line managers)
-
User Access Reviews.
In the last few years, a series of regulations ‒ such as SOX/JSOX, GDPR ‒ has forced organisations to perform User Access Reviews. Conducting these controls can be extremely time-consuming, and slow down the core activity of your business.
In this article, I’ll provide you with best practices for carrying out a smooth User Access Review process.
An example of the challenge one of our clients faced before investing in Soterion for SAP to manage their User Access Reviews: They followed a manual process with spreadsheets to identify numerous conflicts in superfluous access and segregation of duties. Without resources or GRC tools, extracting all the data relating to role user authorisation was taking them several weeks. In total, it took them six months to review hundreds of thousands of rows to identify each compliance risk and to be ready for their audit. This was not a viable process, and led them to use Soterion’s solutions.
Why is the SAP User Access Review so important?
The primary reason for the User Access Review is typically for auditing reasons. Many audit regulations, such as Sarbanes Oxley (SOX) and JSOX, require that listed organisations conduct User Access Reviews at regular intervals, usually once a year.
Before going any further, let's remind ourselves of the objectives of User Access Reviews:
In a given year, requests for changes to SAP access will be simulated using an access control solution. Line managers and business users will be asked to review the proposed changes, with approved requests being implemented in SAP.
The function of the User Access Review is to check whether that SAP access is still valid at a later date. For example, if a person requests access to the Create Purchase Orders (ME21N), the appropriate role will be assigned to the user, if approved. If this assignment was made on 1 January 2020, who is to say whether the access is still relevant for that user on 1 January 2021?
The User Access Review therefore gives the organisation the opportunity to re-examine the user's access to confirm that it is still relevant and applicable (the user may have changed job function or role since the role was assigned). A major benefit of a User Access Review is that it limits SAP authorisation drift.
The disadvantage for many organisations is that the User Access Review is carried out for the sole purpose of appeasing the audit, and the value of this activity is questionable, especially given the amount of effort required by business users to carry out a User Access Review.
There is a need to change the mindset of business users from an auditing exercise to be ‘ticked off’ to a useful activity to address and manage access risks. This should not be driven by a desire to appease auditors, but rather by a commitment to manage access risks.
However, to support this change of mindset, organisations must consider several process changes to support the business. It is important that organisations understand the challenges faced by users performing a SAP User Access Review. If users feel that the user access control process is onerous or difficult, they will push it away and treat it as a tick-box exercise. Result: the organisation will be getting minimal value from the User Access Review.
How do you promote this mindset change?
Besides getting senior management support for the User Access Review, it is critical that a number of technical aspects are considered to make the process easier and simpler for the business users. Here are a few considerations:
1. Role design
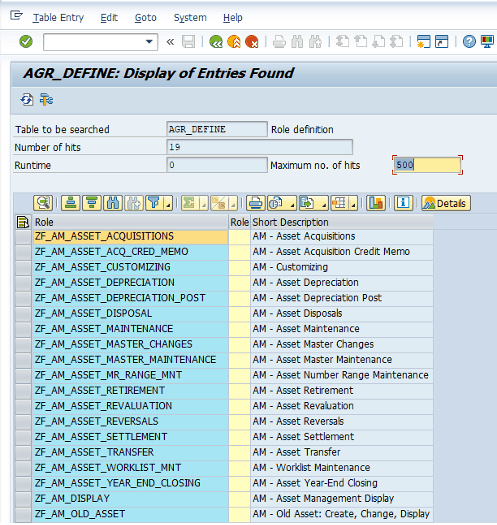 Does the design of the organisation's SAP roles make it difficult for business users to know what access users have, ie are the SAP roles not descriptive? Are the SAP roles large and contain many transaction codes?
Does the design of the organisation's SAP roles make it difficult for business users to know what access users have, ie are the SAP roles not descriptive? Are the SAP roles large and contain many transaction codes?
To make the User Access Review process as simple as possible for the users, ensure that the SAP role design lends itself to simplifying the process. Functional role designs typically have more descriptive role names, making it easier for users to understand the content of the SAP roles under review. This will allow business users to make an informed decision on whether or not access is appropriate for the user.
Updating the role design to be descriptive may in fact require a complete role redesign. The organisation's move to S/4HANA can be an excellent opportunity to re-examine the organisation's security framework and consider a role redesign that is more user-friendly and simpler, reducing the effort required to review user access.
2. Role methodology
Unfortunately, discussing SAP role methodologies is like discussing religion and politics. People become familiar with one role methodology and do not fully appreciate any other methodology. Most SAP security administrators understand a derivative role methodology and have a limited understanding of a task and value (functional/enabling) role methodology.
The task and value role methodology is to separate transactional access from organisational-level access. This means that there are far fewer roles to create and users are assigned fewer roles. Choosing a role methodology with fewer role assignments will reduce the effort required by the business users to perform a User Access Review.
The task and value role methodology is to separate transactional access from organisational level access. This means that there are far fewer roles to create, which also means that users are assigned fewer roles. Choosing a role methodology with fewer role assignments will reduce the effort required by the business users to perform a user access review.
3. Rule-set customisation and business education of access risk
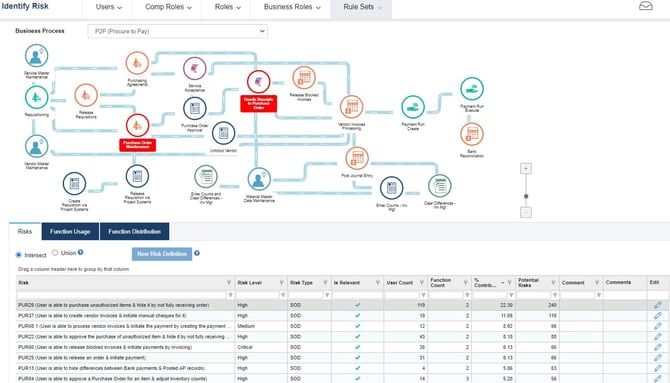
Business users who conduct a User Access Review are likely to pay more attention to the SAP roles assigned to their users that contribute to access risk violations. If the business has completed a rule-set customisation project, it is likely to have defined a more appropriate and refined rule-set.
The draft Access Risk Rule-Set is an excellent tool for advising Business Users of the access risks applicable to their sector. By having a better understanding of each of the access risks in the rule-set, business users can make more informed decisions when reviewing user access to determine whether or not a particular user's access is acceptable.
4. Use a tool to facilitate the User Access Review process
Conducting a User Access Review in a spreadsheet often proves challenging. Although the reviewer can see the roles assigned to the users, spreadsheets often lack usage and risk information. This results in roles with transaction codes being removed from a user (access required by the user to carry out their job function). This leads to disruption of operations and most of the removed accesses are reassigned to these users immediately after the User Access Review.
By using a commercial solution for the User Access Review, the business users can make more informed decisions with user-transaction usage and access risk information.
One of the great advantages of using a tool to facilitate the User Access Review is that it can be configured to speed up the process. For example, a User Access Review can be created to include only those roles that contribute to access risk, reducing the number of role assignments that need to be reviewed. Another example is the creation of a User Access Review that flags previously ‘approved’ roles so that the focus is on new assignments since the last review. For reviewers to perform a User Access Review properly, it is important that the solution converts the technical language of SAP roles into a language that business users can understand.
5. Split reviews
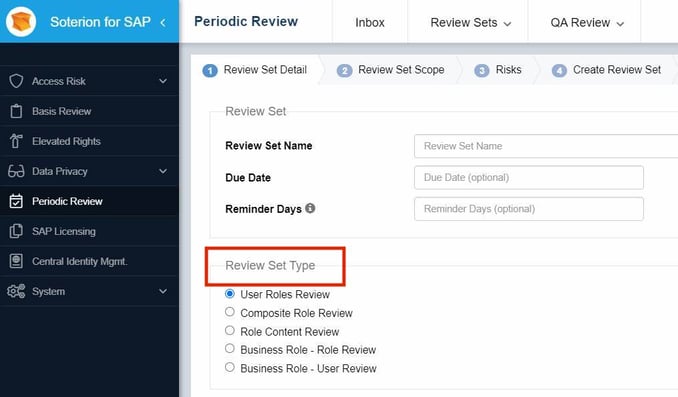
If you make use of SAP Composite or Business Roles, consider splitting the review into a User Access Review and a Role Content Review.
-
Role Content Review: A role owner reviews the content of the SAP Composite or Business Role.
-
User Access Review: A line manager reviews the role assignments at the SAP Composite or Business Role level. They do not review the underlying SAP single roles but simply check whether the Composite or Business Role is appropriate for the user.
6. Iterative reviews
Rather than having one large annual User Access Review, where all users' access is reviewed, see whether it is possible to break it down into smaller iterative reviews over the year. This can be divided by:
-
Geography: User Access Review done by region.
-
Risk level: User Access Review done by risk level.
-
SAP module: Users Access Review done by SAP module.
It is important to bear in mind the challenge of certification fatigue. This is where the reviewers complain about the time and effort required to conduct a User Access Review.
What is Periodic Review Manager by Soterion?
Periodic Review Manager, a module of Soterion’s product suite, is a user-friendly solution that allows your business users to periodically review your SAP user access risk in your SAP systems easily and efficiently. This process will significantly improve the visibility of your GRC environment, and may be an audit and statutory requirement for your organisation.
If you would to know more about Soterion's GRC for SAP tools, check out the features and success stories here: https://www.epiuselabs.com/soterion
To request a demonstration with one of our experts: https://www.epiuselabs.com/request-a-soterion-demo
How can we help you?
Soterion is the market leader in business-centric GRC. By converting the technical GRC language into a language that business users can understand, Soterion facilitates business buy-in and accountability. Find out more about Soterion’s wide range of GRC solutions used
by leading brands ‒ Endeavor, Aker Solutions and Compass Group to name a few, or request a demonstration with one of our experts.
Dudley Cartwright
With over 20 years of SAP Authorization experience, Dudley’s strong technical understanding combined with his sharp business knowledge has allowed him to implement security solutions of the highest quality for companies all around the world. Dudley has a passion for implementing “fit-for-purpose” value-added solutions - a philosophy that has become the cornerstone of Soterion’s mission.