SAP is one of the most robust systems in the world, but also one of the most complex, and SAP’s structure makes addressing data privacy compliance particularly tricky. Based on lessons learnt from multiple complex projects around the world, I have developed a set of essential steps in the implementation approach for data privacy compliance in SAP systems.
SAP is one of the most robust systems in the world, but also one of the most complex, and SAP’s structure makes addressing data privacy compliance particularly tricky. You need detailed domain knowledge to map and understand the cross-functional integration of multiple SAP objects and systems.
Having been an SAP partner for over 30 years, we have an in-depth understanding of how SAP data is structured, and have worked closely with companies around the world, helping them to become compliant with global data privacy legislation such as the GDPR (General Data Protection Regulation).
As of today, there have been at least 20 revised privacy laws enacted around the world, so your company may be subject to a wide range of regulations, and face hefty fines for non-compliance.
Based on lessons learnt from multiple complex data privacy projects around the world, I have developed a set of essential steps in the implementation approach for data privacy compliance in SAP systems.
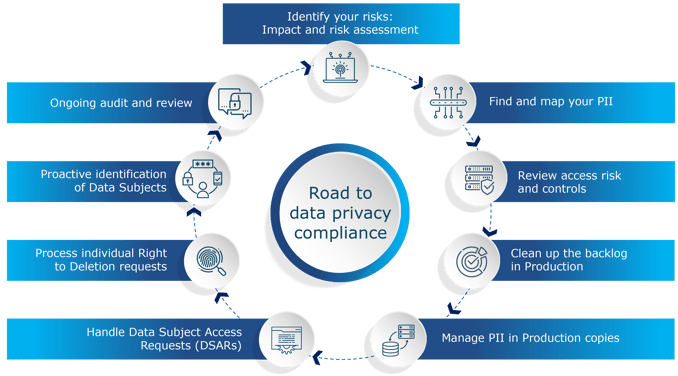
The nine steps are:
- Identify your risks: Impact and risk assessment
- Find and map your PII
- Review access risk and controls
- Clean up the backlog in Production
- Manage PII in Production copies
- Handle Data Subject Access Requests (DSARs)
- Process individual Right to Deletion requests
- Proactive identification of Data Subjects
- Ongoing audit and review
You can explore these steps further in my latest ebook, which provides a practical guide for starting your implementation journey.
Find out how to get started.

James Watson
James is responsible for the global line of business for EPI-USE Labs' data privacy and SAP IS-* Solutions, supporting all regions and key accounts running Data Sync Manager (DSM) for these complex requirements. With a functional and business background of over 20 years, James provides the bridge between Development, Basis, Test/Competency Centres and leadership teams to provide guidance and advise on the route to data privacy compliance. His history includes SAP specialisms in non-production data management and anonymisation, Production data removal or redactions, System Landscape Optimisation (SLO) and SAP industry solutions.