The General Data Protection Regulation (GDPR) is certainly not news any more. Most individuals and companies have adapted to the large (and dare I say annoying) notices around cookies and getting ‘voluntary’ permission to process the individual’s data. You can definitely see there has been a change since May 2018. In general, the public is much more educated that data needs to be protected. But the application of the regulation is not without its problems.
GDPR was a much-needed change to the laws to guide a world where we have become 100% online. And it’s happened relatively fast; our children will never know the sound the modem used to make when you got a turn to quickly check emails.
What are the GDPR principles?
The GDPR is long and complex, with many aspects that organisations need to take into account.
I wanted to look at the principles that underpin the regulations. The ICO’s website is a very good succinct guide about what the principles are.
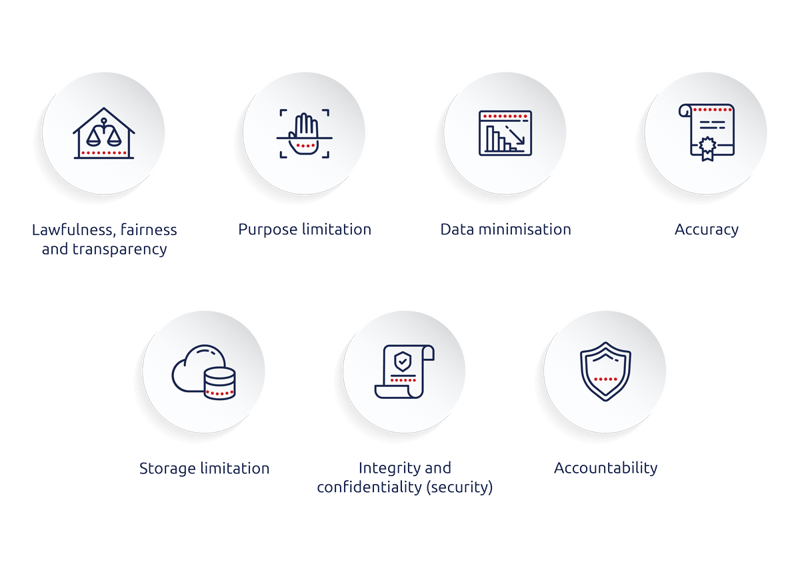
Each of these principles can be used as a guide to show the intent of the regulation. Organisations need to focus on making sure they are fair and lawful when they gather, process and store data from a European citizen.
For this blog, I want to look at integrity and confidentiality (security). With the rise of many data breaches and cyber attacks making headlines globally, the profile and extent of the breaches are getting bigger. One of the most prominent breaches for 2020 was on Twitter, where major accounts were hacked and used to send fake tweets from the account to send money to an unknown Bitcoin address. Another example is where Zoom login details were up for sale as many people started to use the platform during the COVID-19 pandemic.
Cybersecurity = integrity
I want to focus on the Integrity and confidentiality (security) principle. The ICO states that this principle is about organisations being required to have the appropriate systems and processes in place to process data securely. And the way that the security principle is linked to integrity shows that it is clear that security of data is closely correlated with the integrity of the organisation. Your business might be about something completely removed from cybersecurity, but you still need to take this aspect as seriously, because it can reflect negatively on your brand reputation and the integrity of your business.
Certain steps that are recommended include that you start with risk assessments, and map out where your systems might be open to an attack. You need to look at both external and internal threats. According to a study done by Poneman Institute for ObserveIT, the number of insider-caused cybersecurity incidents increased by 47% since 2018. With the prevalence of working from home as part of the COVID-19 response, we expect to see that percentage increase even further, with permanent and contract workers no longer overlooked by their peers in an open-plan office.
Confidentiality reduces the security risks
The second part of this principle is ‘Confidentiality’. As the dictionary states, this is ‘the state of keeping information secret or private’. To adhere to this principle, organisations need to apply, where appropriate, pseudonymisation and encryption measures. Technology will help companies to achieve this.

But when you think about it, confidentiality in SAP systems goes far beyond this first definition; it's also about knowing what data you need in its original form and monitoring access to this information. An easy win is to mask data in your non-production environment. This has been a guideline by SAP too.
More details about GDPR compliance for SAP
SAP is a great solution and will provide you with well-established security mechanisms. But you need to make sure that you have the security principle embedded in your processes. And sometimes take extra steps to ensure you are in line with this security principle, and also in general with GDPR. To add to this, S/4HANA might be your first major project since GDPR came into force and so data privacy must be included as part of the project design, which probably wasn't the case in any of your previous upgrades.
To help our clients with more detailed information and some practical steps to take into consideration, our EPI-USE Labs colleagues Paul Hammersley and Warren Eiserman wrote a white paper that is available here.
Magdaleen Kotzé
Magdaleen is responsible for global marketing at EPI-USE Labs, working in collaboration with the regional marketing and line of business leaders. Having been involved in the SAP industry for the last fifteen years, she has an in-depth understanding of how EPI-USE Labs solutions solve clients' SAP business challenges. She is passionate about listening to our clients and identifying how we can meet their needs effectively. She is also a strong advocate for content marketing and storytelling.
