In this blog post, we provide a quick overview of the POPI Act, how it differs from GDPR, and practical steps you can take towards POPI compliance, specifically for SAP systems.
What and when is POPIA?
The Protection of Personal Information Act (Act No. 4 of 2013), better known as POPI or POPIA, is a South African piece of data privacy legislation. The intended purpose of the Act is to the privacy and integrity of people’s private and sensitive information. It allows South African data subjects, both as natural and juristic persons, to take control over their information and prohibited others from abusing it.
The POPI Act gives a government body, called the Information Regulator, the authority to enforce the law, as well as provide data subjects with a central point of contact when their personal data is being abused.
Although POPIA has been enacted, it will only come into effect once the Information Regulator is officially operational. It is expected that this will happen in 2020. Once POPIA commences, there is a one-year grace period for organizations to comply.
It is hoped that this law will reduce the prevalence of crimes related to personal data, such as identity theft. Watch this video to learn more about POPIA:

POPIA vs GDPR - Similar, with a key difference
The POPI Act was developed shortly after the first drafts of GDPR became available. Consequently, POPIA used GDPR as a template to some extent, leaving the two pieces of legislation with striking similarities.
The table below provides a quick comparison of key areas of both GDPR and POPIA. For a more detailed review, you can read our blog series, starting with this article.
|
POPIA |
GDPR |
|
|
Who must comply? |
“Responsible parties” who decide on the reasons and purpose of data collected, and “operators” who provides data processing services. This can be the same organization. |
“Controllers” who determines the purpose and means of personal data processing, and “processors” who provides data processing services on behalf of controllers. This can be the same organization. |
|
Who is protected? |
A data subject that is either a natural or juristic person |
A data subject that is a natural person |
|
What is protected? |
"Personal information" defined as information relating to an identifiable, living, natural person, and where it is applicable, an identifiable, existing juristic person |
Personal information that can be used to identify a natural person. |
|
How are they protected? |
Lawful basis and consent |
Legal basis and consent |
|
What are the consequences of non-compliance? |
|
|
The two laws are very similar with the major exception of how a data subject is defined. POPIA includes “juristic persons” as data subjects which broadens the definition significantly to potentially includes companies such as vendors or, in B2B operations, client companies. Watch this webinar below to find out more about GDPR and POPIA:

The first steps towards POPIA compliance
Typically, compliance programs start with a Data Privacy Impact Assessment (DPIA) – a mechanism for determining people, processes and systems involved. By undertaking a DPIA, you will be able to identify the main business risks with respect to the rights of data subjects. You can then identify what the risk of processing incorrect or inaccurate personal data may be to your business. During the DPIA, you will identify those processes which interact with your SAP systems.
Steps involved in the DPIA include:
- Plan
- Identify team and stakeholders
- Define scope of the assessment
- Assess
- Track data flows across business process in scope
- Review existing legal and privacy policies
- Determine threats to privacy rights and business vulnerabiltiies
- Determine controls and countermeasures
- Implementation of Controls
- Follow data privacy guidelines
- Determine privacy measures and responsibility matrix
- Design or select security features
- Sign off Report
- Define auditing procedures
- Create follow-up activities
You can find a full example of a DPIA implementation in Making POPIA Compliance Easier (From an SAP Perspective) (a comprehensive white paper).
Key steps to POPIA compliance for SAP systems
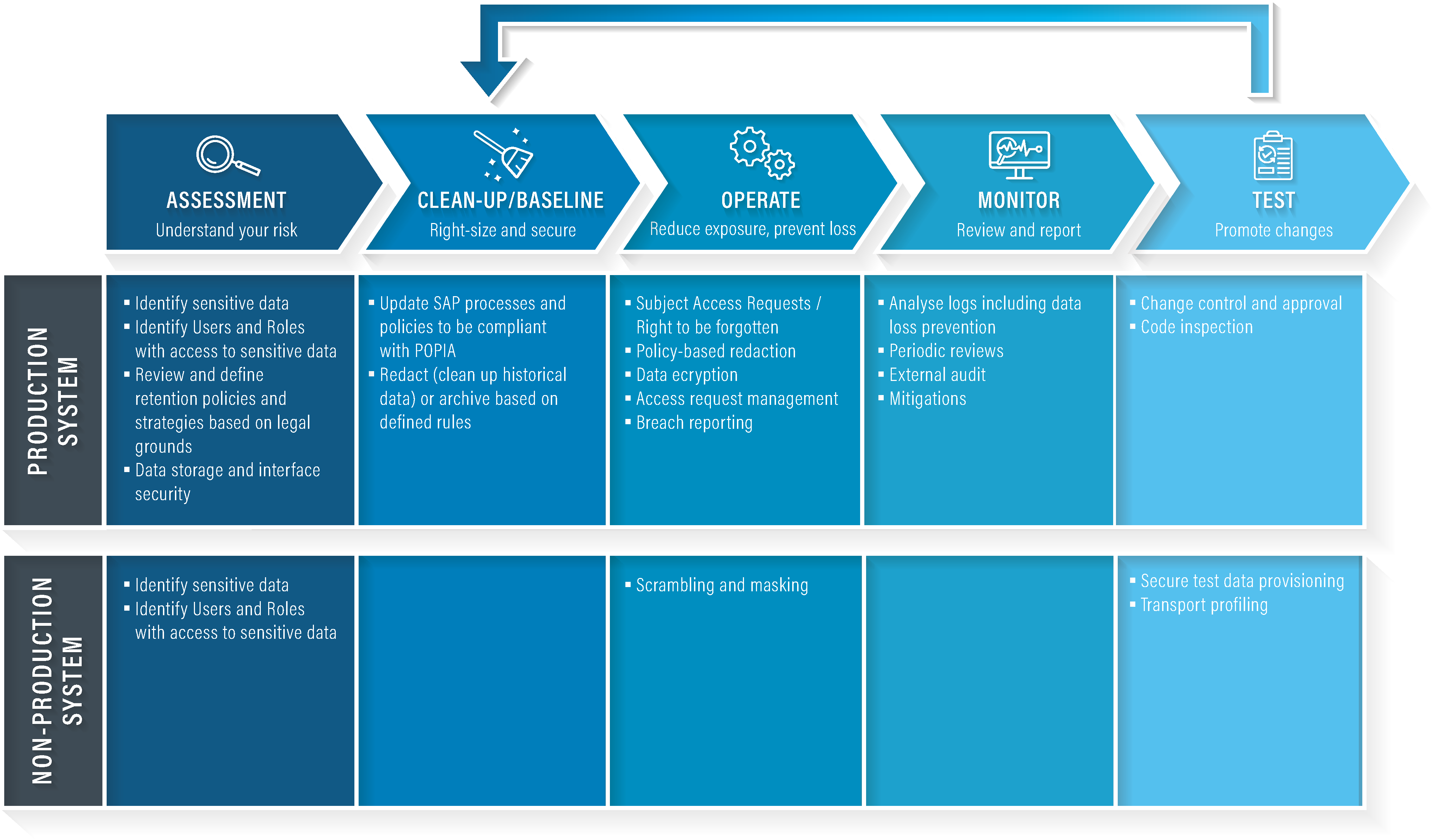
When implementing a POPIA compliance project where SAP systems are involved, there are a number of phases that are typically followed:
- Assessment (a component of the DPIA)
This phase of the compliance project creates a deeper understanding of the risks involved. You’ll review sensitive data, access risk, retention policies, and data storage and interface security. - Clean up / Baseline
In this phase, you update SAP policies and processes to be POPIA compliant and redact any data that may impact on your compliance status. - Operate
During the operation phase, a number of actions are taken to maintain compliance such as scheduled redaction, data subject deletion requests, and breach management. - Monitor
An essential part of ongoing compliance is monitoring. Effective monitoring activities allow you to understand how well processes are maintained, and where improvements can take place. - Test
Finally, during the test phase, changes resulting from the monitoring phase are implemented and further managed.
In our whitepaper, Making POPIA Compliance Easier (From an SAP Perspective), we explore these steps in more detail, provide clear directions on how technology can support your compliance journey, and provide nine recommendations to keep in mind during your compliance project.
Gericke Potgieter
Gericke is responsible for marketing systems management and data analytics at EPI-USE Labs. He is a qualified ISO 27001 Lead Implementer and has an MA in Socio-informatics (Decision Making Theory). He has spent most of his career in IT, strategy consulting and software development.